- AHB | ~root@clover:
- Posts
- 🔗 Chaining Open Redirect & Self-XSS for High One-Click Account Takeover
🔗 Chaining Open Redirect & Self-XSS for High One-Click Account Takeover
A Hacker's Blog | ~root@clover:
The Low Down [TL;DR]:
I discovered a critical vulnerability chain on a target on a private bug bounty program that allowed Full Account Takeover of any user's session. The attack weaponized a seemingly low-risk Self-XSS flaw by chaining it with an Open Redirect flaw. This allowed an attacker to use a single, trusted-looking link to force a logged-in victim's browser to execute the XSS payload, resulting in the theft of their primary ssoui session cookie and complete account compromise.
The Vulnerability
This was a classic example of combining two low-impact vulnerabilities into one critical finding (Severity: High, CVSS 8.7).
1. The Open Redirect (subdomain.target.com)
Flaw: An endpoint designed to handle redirects on
https://subdomain.target.com/close-iframe/had an insufficient regex filter.Exploitation: By appending
/www.target.comto an attacker-controlled domain (e.g.,poc.attacker.xyz), the attacker could bypass the filter and redirect the victim's browser from a trusted subdomain to their own malicious server.
2. The Self-XSS (webftpservice.target.com)
Flaw: An API endpoint (
https://webftpservice.target.com/application/api/api.php) reflected user-supplied data from theconnectionTypeparameter within aPOSTrequest. When a proper XSS payload was supplied, I was able to achieve self-xss via the ftp connection form.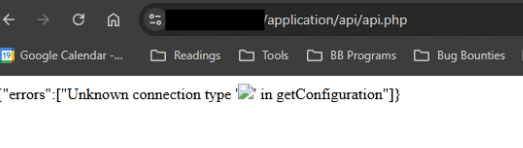
The Problem: Normally, a Self-XSS can be useless and hard to exploit in an impactful manner. But with this Open Redirect vulnerability, if the victim was logged in, I was able to force their browser to perform the necessary cross-domain POST request resulting in me being able to steal their account’s session cookie which would result in full account takeover. Due to a
gotoparameter on this target’ssso.target.comURL I was able to craft a URL that would prompt the user to login upon clicking it, this way I ensured any victim would have a valid login session regardless.
The Account Takeover Chain
Attacker Setup: The attacker hosts a script on
poc.attacker.xyzthat creates a hidden form and automatically submits aPOSTrequest to the vulnerable Self-XSS endpoint onwebftpservice.target.com. The attacker must also modify the.htaccessfile where they’re hosting the malicious script so that when the/www.target.comendpoint is requested on their website it would redirect to the.htmlpage that executes the hidden form request with the malicious payload.RewriteEngine On # Check if the request URI is '/www.target.com' RewriteCond %{REQUEST_URI} ^/www\.target\.com$ [NC] RewriteRule ^.*$ /stoleyoursession.html [L,R=301]The XSS Payload: The POST data includes a JavaScript payload designed to steal the
ssouisession cookie and send it to the attacker's server:JavaScript
The Single-Click Link: The attacker sends the victim the crafted URL, which starts on the trusted SSO domain and uses the Open Redirect to land on the attacker's page:
Impact: The victim clicks, is silently redirected to the attacker's page, their browser silently executes the Self-XSS POST, the XSS fires, and the
ssouisession cookie is stolen, granting the attacker full account access.
Final Thoughts
This vulnerability chain underscores the necessity of a defense-in-depth approach. Security teams must look beyond the immediate severity of individual findings and consider how they can be chained together.
Mitigation for XSS: Strict Context-Aware Output Encoding and a robust Content Security Policy (CSP) are non-negotiable standards for preventing cookie theft.
Mitigation for Redirects: An Allow-List approach for all external redirects is always superior to filter-based solutions.
While my full report was initially duplicated by another researcher who had only reported the Self-XSS as "Informative," the successful combination with the Open Redirect demonstrated the true Critical Impact of the chain, ultimately forcing the full fix. The fix included a one-time CSRF token being added to the form along with a X-Content-Type-Options=nosniff header being added to the server response.
My advice for any researchers/hackers who made it to the bottom here is to always keep digging and try to maximize your impact before reporting low severity reports or moving on from what you may believe is useless. I had found this Self XSS months ago and left it in my ‘Gadgets’ notes only to return to it months later and with curiousity and other puzzle pieces I was able to create a One-Click Account Take Over Chain.
HackerOne Report